
What Is HTTP Tunnel and 7 Best Ways to Bypass Internet Censorship in 2024

This article has been just updated:
The internet is no longer the lawless digital Wild West it used to be not that long ago. Copyright holders and watchdogs relentlessly put pressure on internet service providers to monitor the online activity of their customers, entire governments spy on their citizens and restrict access to websites that don’t support their ideology, and websites themselves collect a plethora of information about their visitors with the intention of selling the collected data to the highest bidder.
Quick navigation:
As bleak as the evolution of the internet may look like to digital freedom advocates, things are not as bad as they could be because there are still ways to bypass internet censorship in 2024. Whether you live in an oppressive country, work for a company that draconically blocks websites you need for work, or just don’t want to share your online activity with your internet service provider, the methods described in this article provide the cloak of invisibility you need to freely roam the internet.

When you type in a URL in your web browser and hit Enter on the keyboard, you set in motion a whole cascade of events that culminate in your browser displaying the requested website.
In most cases, the connection is in part facilitated by at least one proxy server, which sits between your computer and the destination server and acts as an intermediary. But proxies aren’t just simple messengers.
They can also create a direct link between two devices that would otherwise not be able to talk to each other by encapsulating data using the HTTP protocol, creating the so-called HTTP tunnel. You can think of an HTTP tunnel as a string telephone used by two neighboring kids to have secret calls late at night. As long as both parties keep the communication channel open and use a reliable encryption mechanism, they can exchange information in privacy.
Proxy servers and HTTP tunnels are the foundation of many ways to bypass internet censorship in 2024, such as TOR (The Onion Router), open source software that routes internet traffic through multiple proxies for anonymity.
Interesting Coupon Code & Promo Codes Deals:
Norton Antivirus Symantec sale deal are still available. Still open for Linux, MacOS and Windows operators. Everyone has the favor of Norton Antivirus coupon codes. With your tightened budget you can have your device or network secured cheaply. Check out at https://www.coupon-karma.com/norton-antivirus-symantec/ learn more about Norton Antivirus Symantec best coupons that you probably need.
Many people are now developing a direct interest on Wondershare software Apart from the best Wondershare coupon codes The Wondershare manufacturing agency offers the mind mapping tools. The simplified PDF keep the distractions at their minimum level. Wondershare wants every person to share their best moments in life with just a single click.
Over the years Eset has been the most preferred Cyber security firm in the entire world. Their professionals have mastered all the contents internet security. The experts have gone a step further to develop multiple anti-malware product. With more than 100 million clients Eset has gained confidence from their customers in solving all internet security matters. Find Eset sale deals here https://coupon-karma.com/eset/
Avira Antivirus is the major product manufactured by Avira. The multi-national company dealing with computer security software. Avira Antivirus guarantees maximum protection form malwares and viruses. Getting Avira Antivirus is simple and affordable. Learn more about Avira sale deals here. Use Avira software products to feel comfortable and free from losing your data to any third party.
Techsmith is an excellent company offering impressive screen experience. It has over 65 million users all over the world. Techsmith screen sharing abilities offers a new look on phones or computers. Different businesses and companies are competing for the Techsmith promo codes to get Techsmith important aspects used in our modern day business.
In 2024, nobody is anonymous on the internet unless they take certain steps to hide their online activity from prying eyes. Even then, you should always exercise caution and act as if someone was watching your every click.

A Virtual Private Network, or a VPN for short, has quickly become the most popular way to bypass internet censorship. When you connect to a VPN, all your traffic is redirected via an encrypted tunnel to a server belonging to your VPN service provider. It’s the job of the VPN server to complete all requests on your behalf and forward you the results.
The servers contacted by your VPN server never get to see your real IP address. From their point of view, it seems that all requests are coming directly from the VPN server. Even your internet service provider isn’t any wiser because all they see are encrypted data packets flowing through the VPN connection.
VPN service providers like NordVPN, Private Internet Access, and ExpressVPN make it exceptionally simple to establish a VPN connection thanks to their polished client applications and compatibility with all major operating systems. Some VPN service providers even provide obfuscated VPN servers that hide the fact that you’re connecting to the internet via a VPN.
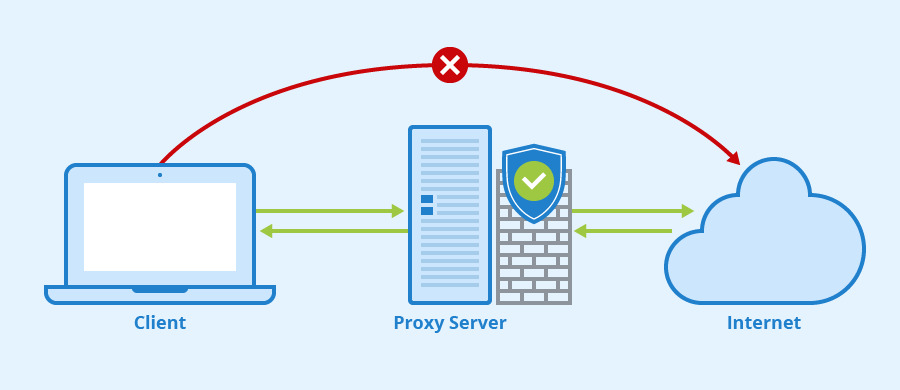
As we’ve already explained, a proxy server is basically an intermediary that sits between your device and a remote server, routing your requests and forwarding responses to them. While some proxy servers protect the privacy of their users, others do not because they leave internet traffic unencrypted.
Proxy servers are most useful in situations where you need to quickly and painlessly access a blocked website and don’t have time to set up a VPN connection. In such situations, you can simply open a web-based proxy server like HideMyAss! or Hide.me in your web browser, enter the URL of the website you want to visit, and hit Enter.
Web-based proxies typically make money by inserting ads into web pages, so we don’t recommend you use them on a regular basis, which is where paid proxy service providers such as ProxyCrawl, NewIPNow, or StormProxies come in, offering premium proxies with unlimited bandwidth in multiple locations around the world.
Tor Browser lets you easily use one of the largest networks for enabling anonymous communication on the internet. The Tor network consists of thousands of relays located in all parts of the world. The purpose of the relays is to randomly bounce traffic until it reaches the end destination, concealing the IP address behind the original request in the process and thus protecting Tor users against internet censorship and mass surveillance.
Because Tor is a free and open source project, anyone can download Tor Browser from its official website and use it without any limitations. Tor Browser is compatible with Windows, macOS, Linux, and Android, and it’s based on Mozilla Firefox.
With Tor Browser, you can anonymously visit websites, watch online videos, or post on social media. Because the capacity of the Tor network is limited, you probably won’t be able to achieve your maximum download and upload speed, so using Tor Browser for day-to-day browsing may turn out to be an exercise in patience.
Secure Shell (SSH) is a cryptographic network protocol that’s used mainly by system administrators for remote logins, but it can also be used to securely tunnel internet traffic, much like a VPN or HTTP tunnel.
To create an SSH tunnel, you need access to an SSH server and know its IP address. You then install an SSH client application such as PuTTY on your device (Linux and macOS come with built-in support for SSH tunneling—no need to install a third-party client) and establish an SSH connection by specifying the server to which you want to connect and entering the correct login and password.
SSH tunneling has its place in the enterprise setting, where it’s used to remotely connect to applications that don’t natively provide other secure means of remote access. Advanced users can also use it to bypass internet censorship, but there are too many other convenient ways to improve privacy on the internet for SSH tunneling to ever become mainstream.
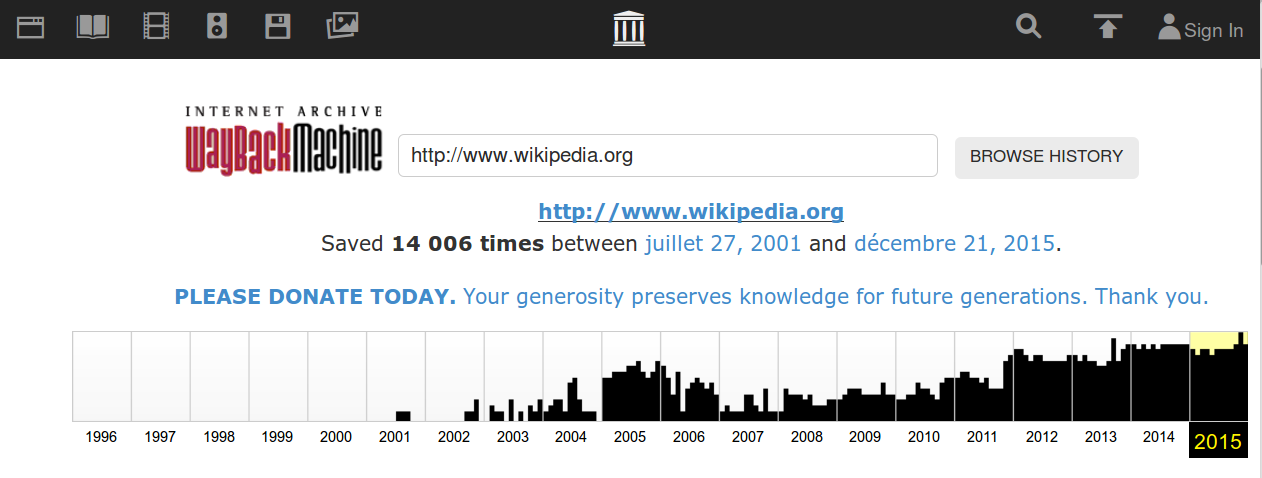
The Wayback Machine is a massive archive of the web. The project launched in 2001, and it has since archived around 406 billion web pages. While its primary purpose is to preserve websites for future generations, you can also use it to access archived copies of sites that are blocked by your internet service provider or government.
To visit a website archived by the Wayback Machine, simply enter its URL or a few words related to a site’s home page and click on the most recent copy. The biggest downside of using the Wayback Machine to bypass internet censorship is the fact that some websites are archived only once in a blue moon, and some are not present in the archive at all.

Ultrasurf is a freeware internet censorship circumvention solution developed by Chinese dissidents, who use it to get around the Great Firewall of China. It bypasses internet censorship using an HTTP proxy server and state-of-the-art encryption. It’s estimated that around 11 million users around the world rely on Ultrasurf to encrypt online communications, hide their IP addresses, and visit blocked websites.
Ultrasurf runs on Windows, but there’s also a version for Android smartphones. To use it, download the executable from its website, extract it anywhere on your computer, and launch it. Ultrasurf will instantly establish a secure connection to one of its servers.
Because its server capacity is limited and the demand from users is constantly growing, you may experience slow response or disconnections, so keep that in mind and don’t expect Ultrasurf to be super-fast.
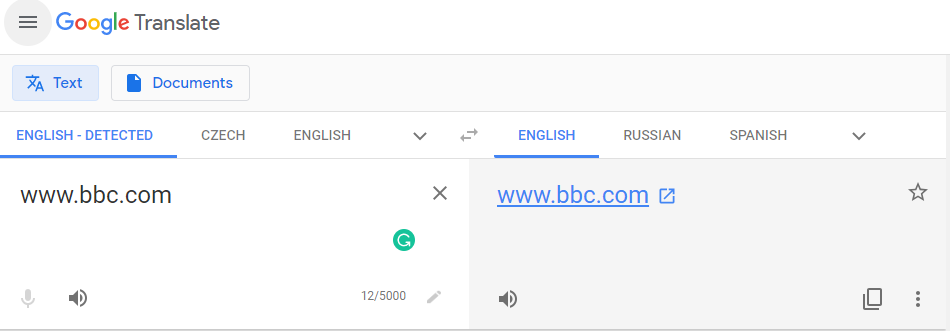
You’re probably familiar with online translation services like Google Translate. What you may not know, however, is that you can use some translation services, including Google Translate, to visit blocked websites.
Google will fetch the website for you and serve it through its servers. To view the original version of the website, all you need to do is click the Original button in the top-right corner.
As an internet user, you’re not entirely defenseless against online censorship. With our seven ways to bypass internet censorship, you can access your favorite websites from anywhere in the world, and browse the web, knowing nobody can see what you’re doing.